Dear Frustrated Enterprise Security Architect,
One of the things I hear the most from Enterprise Security Architects who've been trying to put more "business" in their security architectures with SABSA® is simply this:
"Where am I supposed to start?"
Because, while the standard way SABSA is explained certainly gives you all the parts your security architecture should either reference, include or provide...
...what it doesn't do – by design, actually – is give you any specific guidance on exactly how to discover, document and organize each of the elements it says you're supposed to have.
Of course, there's nothing wrong with this. If you already are an experienced and accomplished architect, assuming that you're actually working to build out true enterprise security architectures that reflect either the security requirements of the solution being delivered or of the organization as a whole, then you probably already have a stable and reliable approach to going quickly from requirements to approved security policies.
Unfortunately...
...many enterprise security architects I've spoken to in the past simply don't have these tools in their toolbox. They constantly struggle when encountering a new project...
...a new business or IT strategy...
...or even when they're brought in to advise on the potential impact of an operational incident...
...because they find themselves ALWAYS starting from either a blank sheet of paper...
...or staring at the 36 cells of the SABSA Architecture Matrix wondering how to translate all the things it mentions...
...into actionable, practical...
...and most of all, USEFUL security architecture documentation.
Well, if that's you, I have some good news for you:
You Don't Have To Do It Anymore!
Because, now that it's been 4 years since I developed the 7 Principles, 14 Practices and 4 Baseline Perspectives™ of The Agile Security System™...
...and helped dozens of people and organizations apply it since then...
...I've come to realize that even though "it's really all there" with what I built in the beginning...
...it's not always easy for people to recognize it—especially when they're in a hurry!
And, as both of us know...
...security architects are never in a hurry, right?
So, based on feedback from people in the field, as well as a thorough analysis and review of all the clients and examples I've provided in the print Security Sanity™ newsletter over the last 4 years...
...I've come up with a set of over 40 worksheets you can use to "feel" your way from requirements to security architecture...
...by effortlessly – and automatically – navigating the most important interdomain trust and value delivery governance relationships between the domains of the Baseline Perspectives...
...thanks to what I call...
The Archistry Architecture Ignition Kit™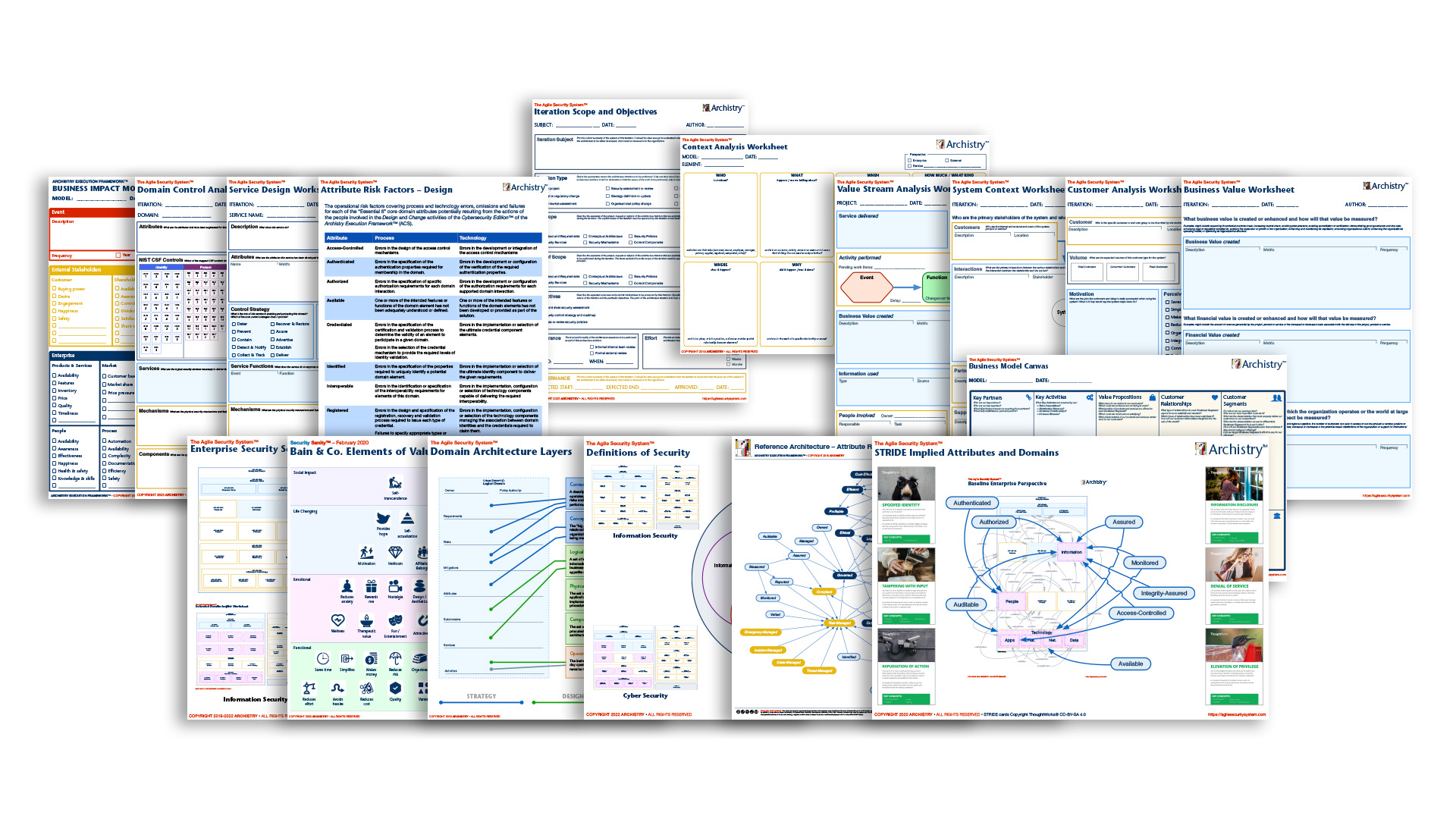
Now, what the Ignition Kit is designed to do is help you think about all the things that are important when designing and documenting a security architecture from the perspective of both the business and risk management. Many of these worksheets have been used internally with clients that pre-date the introduction of The Agile Security System, and that means I know they work. And, based on the early feedback from using them as they are today in the field to tackle real-world architecture problems...
...they don't just work for me...
...they'll likely work for you too.
Of course, like everything, there's some aspect of the "you need to work it" to make it work that goes along with the Ignition Kit in the same way it does for security architecture in any shape, size or form generally.
That's why, if you decide to take advantage of this offer between now and midnight on Sunday, August 20th, US/Eastern time...
...I'm going to give you the "inside scoop" on how to apply the Ignition Kit in the most common ways to the work you do as part of a one-off, first-come, first served Masterclass I'll be hosting live at 1pm US/Eastern on Wednesday August 23.
Don't worry if the timezone doesn't suit you, because it will be recorded – along with the live Q&A session at the end of the session – and it will also be added as a bonus to your content in the Archistry Learning mobile app.
So, if you've been looking for an even easier way to do enterprise, product, project or solution security architecture than I've personally ever seen before...
...at least for the stuff that isn't blindly following someone else's reference architectures, which isn't anything at ALL like what the Ignition Kit is about...
...then scroll on down to the bottom of the page, fill in your details, and I'll see you in the LIVE MASTERCLASS next week.
What You Get
The structure of the Ignition Kit is organized around the different types of things we do as security architects. Specifically, this includes:
- Setting up the architecture iteration and defining its scope and objectives
- Understanding the thing we're supposed to "secure," including it's customers, technical components and external environment
- Using various reference models of the environment, security requirements, threats, definitions of value, and, of course, the Baseline Perspectives and their relationships
- Identifying and prioritizing the various threats and vulnerabilities relevant to the iteration we're performing
- Understanding the primary value and means by which the business "does business"
- Reviewing and selecting the various operational risk factors that are most relevant to the iteration
- Decomposing customer-supplier interactions to understand the trust requirements and value delivery
- Fleshing out the implementation of security requirements and specifying the nature of the necessary security controls
- And, because everyone seems to be doing it, understanding the way the various categories and sub-categories of the NIST CSF are realized in your organization
What I can tell you now, and I will show you next week, is that there are worksheets – and sometimes more than one – that cover each of these scenarios to help you not only think through what's required so you don't miss anything...
...but also so that you can directly take the analysis and synthesis you perform...
...and use it directly to build your Architecture Wall™ and complete whatever security architecture documentation is required.
Why NOW Is The Time To Act
The ongoing fall-out from recent, high-profile breaches – specifically MoveIt and the pain it continues to inflict on its customers and the collateral damage experienced by the ultimate end users – should be more than enough to realize that what we're doing isn't working.
So, that means it's time to try something else.
Now, it's already fast and easy to build SABSA security architectures using The Agile Security System without using the Ignition Kit, but the worksheets help you systematically work though the so-called "spaghetti diagrams" of the Baseline Perspectives focusing on the right sets of core relationships to help you zero in on exactly the parts of your architecture are the most important to you and your security customers.
And, the quicker you grab your copy of the Ignition Kit, the more time you have to play with it before next week's Wednesday live session. That also means you'll have more time to come up with your own great questions that can illuminate what you really want to know about using the Ignition Kit to shed light on the challenges you face every day.
However, before you get too excited and just scroll down to the bottom to grab your copy of the Ignition Kit…
This Isn't Just For Fun
My goal with the Ignition Kit is to help you do your work as a security architect faster, better and more consistently. However, since the Ignition Kit is "just a bunch of PDFs," there's a question that I want to address right from the beginning so there's no confusion about how this is supposed to work.
I want you to conceptualize the entirety of the Ignition Kit as an application like Microsoft Word or some EA modeling tool. While anyone can consume the things you build with those kinds of tools...
...it doesn't mean that anyone can just pick them up and use them.
So, while there's no restrictions on the distribution of populated versions of the Ignition Kit worksheets and templates...
...there ARE restrictions on who can use them.
Specifically, if you decide to take advantage of this pretty crazy offer with the bonus LIVE masterclass on how to use them...
...you are getting a license for YOU AND ONLY YOU.
It's not a license for your whole team, other people within the team or the whole organization to go off, copy the templates into some other format...
...and claim that it's ok.
It's not.
So, I want the licensing to be pretty clear.
It's simple.
But it's also clear.
One purchase = one license for content creation with the Ignition Kit templates.
The output can be shared unrestrictedly. But the structure and content of the templates may not.
If there are problems with this, then please let me know. And, if you want to talk about options for bulk licensing, then that's fine too.
But the bottom line is pretty simple. You're buying a single "seat" to use your copy of the blank Ignition Kit templates as often as you want, as widely as you want.
You just can't let anyone else use them.
And you can't try to claim them as your own.
So, with that legal and procedural stuff out of the way...
...there's not much else left for me to say about it.
Other than if you've ever been looking for the proverbial "architecture cookbook" you could go to each and every time you were trying to figure out what "security" should look like...
...no matter what kind of problem, scope or issue you were dealing with...
...then that's EXACTLY what the Ignition Kit was created to do.
Let’s Get Started!
All you need to do to get IMMEDIATE access to all 40+ worksheets included in the Ignition Kit and start applying them to your own security architecture projects is to fill in the information below, submit the form, and check the home page of the Archistry Learning mobile app.
Once the purchase is confirmed, the automatic provisioning process should give you immediate access, and you can be on your way.
And, no, you don't need to keep the PDFs on your phone. They're easily exportable to other devices using the built-in PDF reader in the app. However, they do remain an ever-available point of quick reference whenever and wherever you need them...
...since they're always going to be on your phone.
All you need to do now is decide to take action, grab your copy of the Ignition Kit using the form below...
...and be sure to block out 2 hours from 1pm US/Eastern next Wednesday, August 23rd for the Live Masterclass and Q&A session.
The way you build security architectures from here forward – with or without SABSA – will most certainly never be the same.
Stay safe,
—
Andrew S. Townley
Archistry Chief Executive
If you have any problems accessing the Ignition Kit, please direct them to custsrv@archistry.com
What People Are Saying About Andrew
A True Thought Leader
“Andrew is a highly skilled and experienced architect and consultant. He is innovative in his thinking and a true Thought Leader in his specialist domains of knowledge—in particular the management of risk. Andrew has also been a significant contributor to expanding the SABSA body of knowledge.”
John Sherwood – SABSA® Creator and Chief Architect
Makes Things Work
“Fabulous person to work with. Very engaging and insightful. Extremely good technical knowledge with ability to relate concepts together and overcome differing opinions. Makes things work.”
Kevin Howe-Patterson – Chief Architect, Nortel - Wireless Data Services
Clarity, Depth and Breadth
“Andrew was able to bring clarity and great depth of knowledge to the table. His breadth of thinking and understanding of the business and technical issues along with a clear and effective communication style were of great benefit.”
Doug Reynolds – Product Manager, MobileAware
Fabulous Consultant
“Andrew is a fabulous consultant and presenter that you simply enjoy listening to as he manages to develop highly sophisticated subjects in a very understandable way. His experience is actually surprising!”
Biljana Cerin, Director, Information Security and Compliance
Interesting, Useful and Full of Ideas
“Found the link to the July issue and read through this afternoon. Think you’ve done a really good job with it and especially around the objective of it being interesting, useful and full of ideas—which the newsletter easily met. Really looking forward to the September issue. If, in the unlikely event an August addition become available, I would happily purchase!”
Andy Smith – Security Architect
More Value Than Anything Out There
"As you have mentioned before, it always all about controls and frameworks. The gap between where the industry is and where we should be seems to be about 180 degrees. Whenever someone asks the question, 'should we have a framework to align business to security?' well they need to look at what Archistry offers. I refuse to pay for any other training class out there. No value after taking BESA, and it's the reason why I spend my money on Security Sanity instead. Absolutely more value there."
Tereston Bertrand – Enterprise Security Architect
A Source of Sanity
“I have been working flat out the last 2-3 weeks on a very detailed program. The one thing that has kept me sane has been your daily emails about the Archistry training. Keep those great emails coming!”
Shane Tully – Enterprise Security Architect
Compelled to Subscribe
"Reading your blogs and content I was rolling at some of the references you make. You write like the frustration of the past guides your fingers across the keys. I was compelled to subscribe to the newsletter."
Vince Nalin – Enterprise Security Architect
Thought-Provoking, Practical Ideas
"Your thought-provoking messages about security, leadership … are welcome. I enjoy reading them. There are many ideas which can be applied to the work, even within the limits of a heavily-regulated organization like my employer."
Helvi Salminen – Information Security Manager