
$22 billion in losses by businesses per year.
$11 million in fraudulent charges.
50 enforcement actions by the US FTC in the last 10 years.
1.2 billion usernames and passwords and 500 million email addresses from 420,000 websites.
63,437 security incidents in 95 countries.
79 seconds between thefts of personal data.
$3.5 million is the average cost of data breach.
$332 million in diminished brand value resulting from losses of customer data.
12 months to restore reputation after loss of customer data.
All of those are pretty scary numbers, and I’m sure you’ve seen many of them before. Normally, statistics like this are used primarily to sow fear, uncertainty and doubt (FUD) amongst potential customers by information security product vendors.
Not this time, however.
This time, we’re pointing these out so you’re not blindsided by them the next time you’re approached by a vendor, and you can be prepared to take considered action to actually do what’s necessary to discharge your duties and obligation as a board member, ensure your customers and stakeholders are appropriately protected and protect the value of your organization’s brand and reputation.
Forewarned is forearmed, as they say.
What exactly is cybersecurity?
Despite all the media hype lately, cybersecurity is really just protecting computers, networks, software and data from inappropriate access, changes or harm. It’s another word for information security, and it focuses on protecting the confidentiality, integrity and availability of systems, networks and data both on an ongoing basis and in the event of unexpected events like natural disasters or other disruptions.
Today, cybersecurity is also very important in ensuring society’s critical infrastructure like power stations, sewage and water treatment, telecommunications and transport are resilient to intentional or accidental disruption. Unfortunately, events like the 2008 Georgian conflict, the 2010 Stuxnet attack against Iran’s nuclear program and repeated interruptions of access to the public Internet by China whenever it suits them and by many other governments during the 2011 “Arab Spring” show that the role of both public and private sector organizations in delivering critical infrastructure can’t be underestimated.
From the perspective of the Board, your responsibilities are to ensure that sufficient controls have been deployed to manage all appropriate risks to your organization’s systems, networks and data. This means you’ve clearly established the overall risk appetite and priorities relating to cybersecurity, and you can demonstrate that the appropriate controls are in place and working.
So, the short version is: cybersecurity is something you’re already doing, but the bad news is you’re probably not doing it very well.
What’s the big deal?
You may think that if you already have an information security program or that IT is handling information security, why is this such a big deal now? There have always been breaches, and there have always been losses. What’s different?
For starters, the overall scope of the problem has increased dramatically in recent years. In this year’s Data Breach Investigation Report from Verizon, they cataloged over 60,000 cybersecurity incidents in 95 countries, and of those, there were 1,367 cases where data losses were confirmed.
Only 2% of the incidents resulting in actual data losses may seem like a small number, but the previous year’s report had over 47,000 incidents and only 621 confirmed cases of data loss. The findings represent a year-on-year increase of 100%!
According to law firm Akin Gump’s annual Top Topics for Directors, cybersecurity is ranked second, and it also ranks 3rd and 4th in the Conference Board’s CEO Challenge list of hot-button issues for the US and Europe, respectively (see Figure 1). However, the overall global ranking is 7th out of 13 issues identified by the survey.
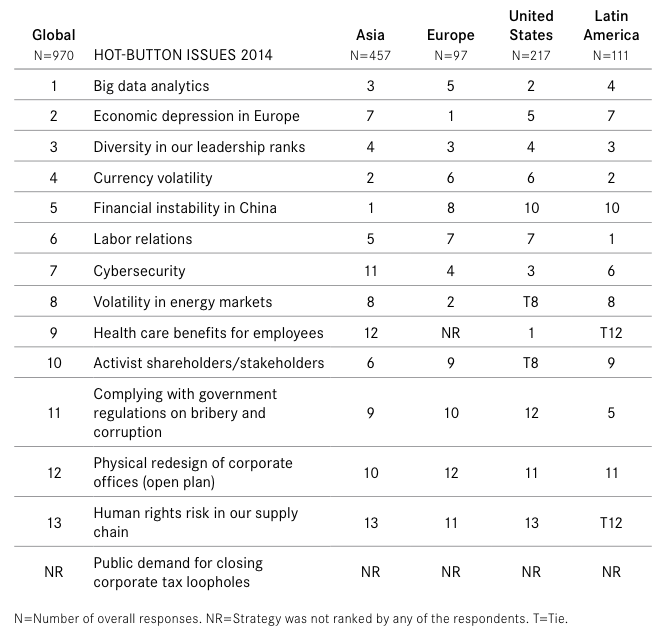
The rankings overall for cybersecurity by the survey respondents seem to indicate an attitude that cybersecurity is something you can solve in a reactive manner and get back to doing what it is you were doing. Unfortunately, much of the available information on cybersecurity reinforces this behavior by stressing the types of controls you need to apply so that you’re protected from the most common types of attacks.
This simply isn’t true.
What you need to know as a board member is that cybersecurity affects nearly every part of what your organization does. The whole point of cybersecurity is to provide an environment where your risks to achieving your objectives are managed so that your people feel safe and confident in executing your strategy. That’s the definition of security, remember? The “cyber” part just means it’s focused on the technology components your organization uses every day to get the job done.
The events spawning the statistics at the beginning of this article have concrete, tangible effects on the bottom line in terms of fines, unexpected expenditures and other business losses due to negative reputational impacts, and they are very real. However, this incident and data breach focus is only a small part of the overall cybersecurity story.
Why you’re doing it wrong
It has been clearly established that corporate reputation is a function of the following attributes:
- quality of management;
- quality of products or services;
- long-term investment value;
- innovativeness;
- financial soundness;
- ability to attract, develop and keep talented people;
- community and environmental responsibility; and
- use of corporate assets.
That means that your organization’s brand and reputation is a valuable strategic asset that is a function of doing other things right. A strong reputation allows your organization to more easily hold off competition from new entrants, charge higher prices than competing firms, attract and retain the best talent, access investors and access capital markets and, more importantly, give your organization a “forgiveness factor” because customers, investors and employees know that occasional mistakes, recalls and performance gaps aren’t “business as usual.”
In my mind, this makes Brand, Reputation and Customer Trust the most important strategic assets of your organization, so everything else you do should be aligned to protecting, enhancing and expanding them. It also means the importance of managing risks to reputation and trust should be one of the clearest messages the Board sends to the rest of the organization.
The inescapable fact is that the Board is ultimately accountable for the organization’s reputation. Therefore, it’s up to you to make sure it’s not in danger.
In today’s business environment, there’s almost nothing you do that doesn’t depend on access and availability to applications, systems and data. If you’re treating cybersecurity as a hot button issue and attempting to throw vendor-recommended controls at it and hope the problem is solved, your own organization is in serious trouble.
You don’t believe me?
Let’s look at some of those CEO challenges again (see Figure 2).
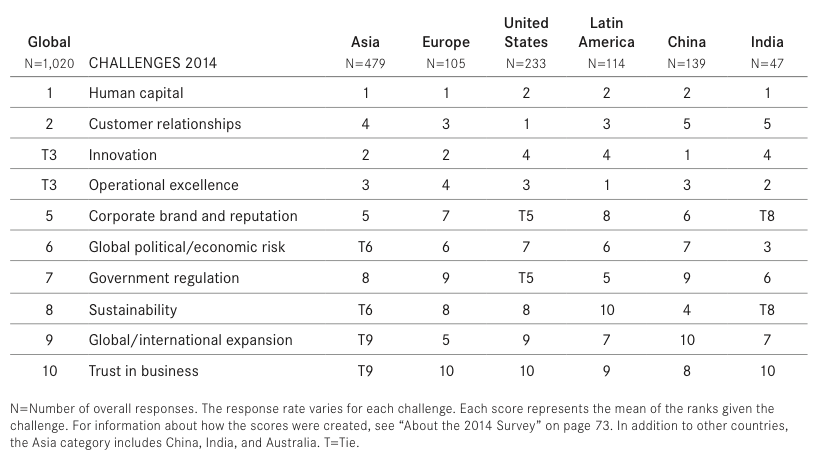
Human capital
This challenge covers the “full spectrum of the employee/employer experience” including attracting, rewarding, and retaining talent. If you aren’t able to guarantee the timely availability and access by your people to the information they need to do their jobs, it isn’t going to develop a strong level of employee commitment. More likely, it’s going to lead to a lot of frustration, inefficiencies and negative views in the marketplace of your organization as a great place to work.
Cybersecurity is what you get when you manage the risks associated with the timeliness, availability and access to the systems and information your employees need to do their job. It means you have controls in place to prevent system disruptions and unauthorized modification and deletion of key business information by people inside your organization.
Managing these risks – creating a secure, “cyber” environment enables addressing the human capital challenge with respect to the tools and information your people need to do their jobs.
Customer relationships
This challenge is all about the way you engage, acquire, service and retain your customers. According to Ponemon’s 2014 survey, poor customer service was the #1 impact on organizational reputation according to 75% of the respondents. The next important ones were an environmental incident (33%) and a data breach (30%).
That means all the FUD about reputation losses in the press and most of those scary numbers at the beginning of the article only represent 40% of the risk to the respondent’s view of the organization’s reputation. Only 40%! And, unless you really screw the pooch, you’ll likely be able to recover your reputation in under a year anyway.
Customer interactions are where the biggest cybersecurity vulnerabilities are, according to the Verizon survey, and they’re also where the majority of the headline-making data breach incidents occur. All of the touch-points with the customer, e.g. web applications, mobile applications, POS systems, and card readers need to be designed, developed and operated to ensure they are easy to use, available, accessible and provide ways to ensure only authorized access to the data exchanged with customers.
Again, all of these characteristics come from appropriately managing the risks that will prevent them from being present. The approach to cybersecurity to ensure these characteristics are present for all customer interactions and handling of customer data must still be selected, deployed and operated according to the Board’s risk appetite for reputational risk exposures.
There must be a clear link from the Board’s accountability for the organizational reputation all the way down to the specific controls used to prevent unauthorized access to customer-facing applications. Without that linkage, there is no way the Board can reliably demonstrate it’s meeting its responsibilities to the company and shareholders.
Operational excellence
This challenge is all about how effective your organization is in doing what’s necessary to execute your business strategy. How well your organization meets this challenge is entirely up to the effectiveness of the Board and the executive team.
Executing day-to-day operations requires that all of the linkages between people, processes and technology fit just right and consistently perform when, where and how they need to in order to deliver your business objectives. Access to business information and systems by employees, partners and suppliers in a reliable and timely manner can make the difference between implementing your strategy or falling into the strategy gap.
Think there’s no place here for cybersecurity? Think again.
Unapproved or malicious use of organizational resources by employees or other internal stakeholders was responsible for 18% of the incidents reported in the Verizon survey and 8% of the data breaches in 2013. That’s almost 12,000 incidents and over 1,000 data breaches.
Physical theft and loss of organization information and assets counted for 14% of the reported incidents—nearly as high as unapproved or malicious use. However, less than 1% of these incidents resulted in reported data breaches.
It’s pretty hard to give the partner investment pitch if the only copy is on the laptop you left in the taxi because you were running late for the flight. The critical business information to execute your strategy wasn’t very available now was it?
The Verizon survey also includes a category called “Miscellaneous Errors” and an observation that highlights “repetitive and mundane business processes involving sensitive info are particularly error prone.” It also states that this category contains more incidents by business partners than the others.
You don’t even have to back up and squint to realize that Verizon’s “Miscellaneous Errors” are incidents of operational risk management failures. It’s what happens when people make mistakes. They send the wrong document to the wrong customer, or they put an internal document in the wrong folder and it ends up on the first page of Google’s search results.
These are only a few of the reasons we’re so adamant that successful strategy execution is synonymous with successful operational risk management.
How to do cybersecurity right
There are several aspects to ensuring you take the right approach to cybersecurity. As we’ve already seen, it can’t be just about preventing data breaches or deploying security hardware and controls. Everything needs to fit together in a coherent way.
There are legal and regulatory aspects to cybersecurity. In the US, 33 states have laws ensuring social security numbers are protected, and 10 states have laws explicitly targeted towards protecting personal information. At the federal level, the Federal Trade Commission enforces three laws protecting consumer data, but the majority of their enforcement focus comes from the legislation enacting the FTC that gives them broad powers to determine if organizations are being “deceptive” or “unfair” in their treatment of customers.
In Europe, the EU Data Protection Act and it’s individual ratifications in the 28 EU member states also provides specific legal requirements for the handling and disclosure of personal information for any company handling the information of an EU citizen, regardless if the company has a physical presence in the EU or not. Then there’s also that crazy cookie law from 2011.
Given that cybersecurity is a key enabler to nearly every attribute of corporate brand and reputation, it is rather fascinating that in the proposed strategies to address the CEO challenge of reputation, risk and compliance activities are 11th and 12th out of 15 proposed strategies (see Figure 3). This is crazy!
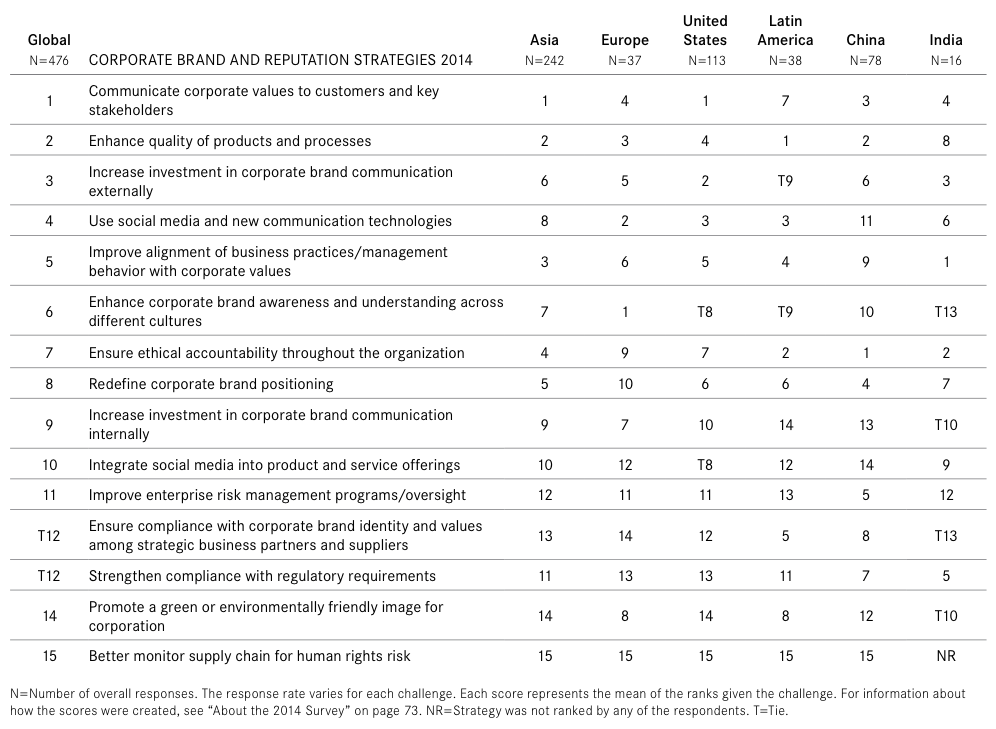
This severe disconnect between a top 5 “Hot Button” issue in the US and Europe and the priority of risk and compliance – both key components of cybersecurity – would indicate a lack of understanding of the pervasiveness and function of cybersecurity by the executive teams of the respondent organizations.
Cybersecurity exists only if the relevant risks to the organization’s information systems, technology and data are appropriately managed within the overall risk appetite of the organization. It doesn’t happen by accident, and it doesn’t happen by following ‘best practice” or deploying a bunch of controls recommended by governments, vendors or industry associations.
Cybersecurity is a result of applying a coordinated, structured and enterprise-wide risk management program to identify the risks associated with confidently and safely accessing business information and systems by employees, customers, investors and other stakeholders during the course of carrying out normal business activities to implement the organizational business strategy.
It requires clear, well-defined boundaries of risk ownership, accountability and structured information exchanges that are enabled by systems and controls carefully selected and deployed based on the risk appetite of each risk owner in the overall context of the Board’s risk appetite and strategic priorities.
No more. No less. No whiz-bang, “techy stuff”.
I hope it’s clear now what cybersecurity is and why it should be a priority for boards.
Cybersecurity, despite it’s rather unfortunate name, is not “a technology thing” to be delegated to experts. Cybersecurity is about risk.
Sure you need specialists in the design and implementation of security architecture and the selection, deployment and operation of security controls. Those are the “techy bits,” but they’re chosen and applied based on your overall requirements, risk appetite and priorities as a board. The technology and security specialists are experts in their fields, but they are only delivering to your risk control objectives.
You own the risk. You always have, and you always will.
If you want to know more or understand what it takes to really address cybersecurity as part of an deliberate and structured risk management and assurance program, please give us a call or fill in the form at the bottom of the page. We don’t want to see you in the papers because of cybersecurity failures or data breaches any more than you do. Let us work with you to ensure it doesn’t happen.
References
- 2014 Data Breach Investigations Report, Verizon Enterprise Solutions, 2014.
- Aftermath of a Data Breach Study, Ponemon Institute LLC, 2012.
- Aftermath of a Mega Data Breach: Consumer Sentiment, Ponemon Institute LLC, 2014.
- CEO Challenge 2014: People and Performance, The Conference Board, 2014.
- Cost of a Data Breach, Safetica, 2010
- IMPACT: Measuring the Loss of Brand and Business Reputation after a Data Breach, Technology Law Source, Porter Wright Morris & Arthur LLP, 2011.
- Information Exposed: Historical Examination of Data Breaches in New York State, Office of New York State Attorney General, 2014.
- Reputation Impact of a Data Breach: U.S. Study of Executives & Managers, Ponemon Institute LLC, 2011.
- Target data breach has lingering effect on customer service, reputation scores, The Wall Street Journal, 2014.
- The Federal Trade Commission’s Role in Online Security: Data Protector or Dictator?, The Heritage Foundation, 2014.
- Top 10 Topics for Directors in 2014, Akin Gump Strauss Hauer & Feld LLP, 2013.
- Unlocking the Secrets of Cybersecurity, University of Maryland University College, 2013.
- What’s in a Name? Reputation Building and Corporate Strategy, Fombrun, C., M. Shanley,, Academy of Management Journal, June, 1990.
