If you’re familiar with SABSA, but you’re still struggling to figure out how to integrate it into the work you do every day, you’re not alone. In fact, based on the conversations we have every day with people who’ve done the Official SABSA Certification training program, it’s probably the number one issue people face:
How do I actually use what I’ve learned in my organization without doubling my workload or “selling” the rest of the team or the organization on SABSA?
Unfortunately, the answer is only readily apparent after you’ve actually worked with SABSA in solving real-world security problems. We’ve been doing SABSA since 2005, helping organizations around the world adopt it within their security programs, and it still took us 14 years to figure out how to explain what we were actually doing and separate that from the mechanics of trying to capture and represent it.
Traceability Tangles
The reality is that to do SABSA correctly can be very data-intensive, and, like many things, the traceability concept which is one of SABSA’s great strengths tends to end up being one of the biggest reasons people get overwhelmed when they try to build SABSA security architectures.
In the course of our practice, we’ve developed sets of templates and worksheets to capture the information used to create and document security architecture probably starting from the same place you did—the worksheets provided with the SABSA Foundation workshops. But in doing so, you can easily fall into the trap of capturing too much information or getting lost in a rat’s nest of “potentially useful” links that add more overhead than immediate value.
You see, SABSA’s simple 2-way traceability through the architecture layers easily explodes into n-way traceability when you’re doing formalized Requirements Engineering. This isn’t necessarily bad, because the expressiveness and the multidimensional links give you a lot of power and proof that you’re really building architectures aligned with the business…
…but, again, it’s certainly overwhelming to try and figure out on your own, when you’re already stuck with an overflowing inbox and just don’t have the time or the energy to try and figure out the right way to start.
Lost In the Matrix
The other biggest pitfall in our experience is fixating on the SABSA Architecture Matrix itself as the fundamental expression of what SABSA really is. Remember, SABSA is a framework and methodology for building business-driven, risk-proportional security architectures you can prove really will deliver value and protect the organization. But as a framework, the Architecture Matrix is not a template to be completed.
It’s a way to structure your thinking so you make sure you haven’t missed anything important.
And, given the principle that SABSA can be used and integrated with any delivery methodology – past, present or future – it also shows you what you need to consider and prioritize when you’re figuring out how to integrate it into what your organization does.
If you’re currently feeling a bit overwhelmed and “lost in the Matrix” when it comes to SABSA, then our program, Lost In the Matrix, might be just the thing to help you escape.
Grab-N-Go vs. Custom Tailoring
However, again, to do this effectively takes a lot of time and deep thinking about your current processes, where you can fit SABSA in to them today, and how using SABSA might drive future improvements. It’s just not easy, and there aren’t really any shortcuts if you want to figure this out on your own.
We’ve been through this process, and as we said before, it took about 14 years over many organizations and many industries and many different problems to make sure nothing essential was missing, and that there was a foundation in place to allow maturity in both process, formality and tooling for the future.
If you have the time and the commitment to integrate SABSA into your organization, you can figure it out. It isn’t easy, but it’s possible. And if you want help doing it instead, we’ve done that too.
However, our approach today is to provide a complete, fully flexible, yet complete approach you can use from today to start building better security architectures for the projects you have on your desk right now based on 7 core principles, 14 practices and 3 perspectives we’ve found represent the essential parts of every organization we’ve ever worked with. We call it…
The Agile Security System™
And by applying it to the problems you’re trying to solve, you will automatically build SABSA security architectures easier and faster than any other way we’ve seen—and we’ve been active members of the SABSA community since 2005, not to mention having the privilege to call John, David and Andy personal friends.
You’re probably pretty skeptical of this claim if you’ve been through the training and tried to apply SABSA yourself to your own organization. We would be too. That’s why before we completely re-vamped our flagship, 7-week, fully-interactive online training course Building Effective Security Architectures, we wanted to be sure we could back up our claims of being able to create actionable SABSA security architectures in hours instead of weeks or months.
The 2-Hour Enterprise Security Architecture
One of the biggest misconceptions about SABSA is that it’s big and heavy. It’s understandable to think this when you see the 36 cells of the SABSA matrix or when you think about applying SABSA in the context of other frameworks like TOGAF®. The reality is that building an effective security architecture for your organization isn’t that hard—if you have a system.
Fortunately, after building and using our own approach to applying SABSA over the course of 14 years across many industries with large and small organizations around the world, we’ve distilled SABSA down to the essentials in what we call The Agile Security System™:
- 7 Principles to guide your thinking and behavior
- 14 Practices to guide your actions and build into daily habits
- 3 core views of any organization we’ve ever seen we call Baseline Perspectives™
Using these elements, first presented in the August 2019 issue of the paid Security Sanity™ print newsletter and covered in each monthly issue since then, you have the most effective, fastest and most constant approach to build SABSA security architectures we think there is. To see what happened when our Founder and Chief Executive, Andrew Townley, first used the system to build an initial Enterprise Security Architecture for a legacy system replacement project in just 2 hours, check out this post on the blog: The 2-Hour ESA: fact or fiction.
It’s also the only real way we know to effectively link your enterprise-wide security polices to your automated CI/CD development pipeline in DevOps, going beyond DevSecOps to deliver truly Agile Security. To see our latest posts on The Agile Security System, check out our blog.
The Cybersecurity Edition™ of The Archistry Execution Framework™
It’s all well and good to learn the SABSA framework, but if you, like many others, struggle to put it into practice, then you’re really wasting your investments in time and money. One of the things Archistry has done is defined a comprehensive approach to applying SABSA and creating a security organization built to deliver on the promises of the methodology. This approach is the Archistry Execution Framework™ (AEF), and we have a specific way to apply it for cybersecurity called the Cybersecurity Edition™ (ACS) which is described in the sample issue of the Security Sanity™ print newsletter and a couple of other bonuses, like the 22 essential steps required to deliver the 4 phases of the SABSA lifecycle, and how SABSA relates to the categories of the NIST CSF and the NIST NICE workforce skills framework.
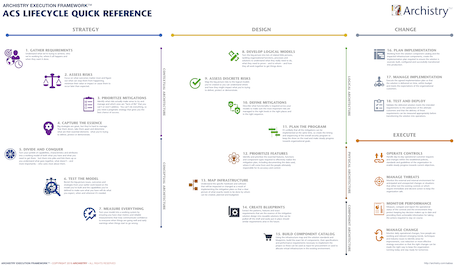
To get it, just sign up to our mailing list on the home page or right here on this page and check your inbox. You’ll immediately get the bonus downloads, and you’ll start seeing what you can do right away to start applying SABSA in your organization.
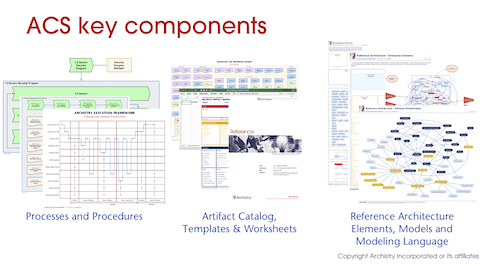
The Cybersecurity Edition grew out of Archistry’s own practice building enterprise security architecture deliverables for our customers and clients and later, out of our work with organizations to transform their security programs around end-to-end adoption of SABSA. The ACS includes detailed processes and procedures, a comprehensive artifact catalog with templates and worksheets you can immediately apply today to start building your own organization’s security architecture and connect business strategy to security operations. The final piece of the ACS is a reference architecture and modeling language for constantly creating your architecture models.
To find out more about how you can get started with SABSA in your own organization, just reach out, and we’ll be happy to talk to you and see whether we’re able to help.
To read more about SABSA and our use of it, check out our latest SABSA posts and our posts on Agile Security and The Agile Security System or you can also get our book, Getting Started with The Agile Security System™. You can also find some videos on what practical applications of SABSA look like on our YouTube channel.
And to get practical examples of using SABSA and The Agile Security System in your inbox every day, don’t forget to sign up for our emails and get the SABSA infographic and guidance for building a SABSA-ready security team as a thank you from us.
If you’re interested in learning how to apply The Agile Security System directly in your own organization, you might want to consider being a member of our next cohort of our flagship learning experience, Building Effective Security Architectures, a 7-week intensive program to develop practical security architecture skills you can use immediately in your own organization, no matter what the organizational structure, no matter what the politics, and no matter whether or not “SABSA” is considered a dirty word, heavy-weight and overly-complex framework that might not even be possible to implement in practice.
To find out more about the program and decide whether it might be for you, then have a look at the course overview and description.
And if you’re currently working on implementing Secure by Design, then check out our newest program, Secure by Design: Step-by-Step.
Our Classic SABSA Intro
Finally, here’s our original overview video about SABSA from 2015, when The Archistry Execution Framework was in an early form and well before the simplification and streaming of The Agile Security System was ever imagined.
